Athena Cyber Hub
Athena Cyber Hub (ACH) is a forked version of Vanilla Control Center with several differences in order to fit the needs of Cyber Security users on Athena OS. It is intended to run vulnerable laboratories for learning purposes and cyber security platforms for offensive and defensive activities.
Athena OS Cyber Hub can be run by clicking its icon in the Application List or running athena-cyber-hub in the terminal.
It provides three sections:
- Cyber Platform Center
- Vulnerability Lab
- Cyber Lab
Cyber Platform Center
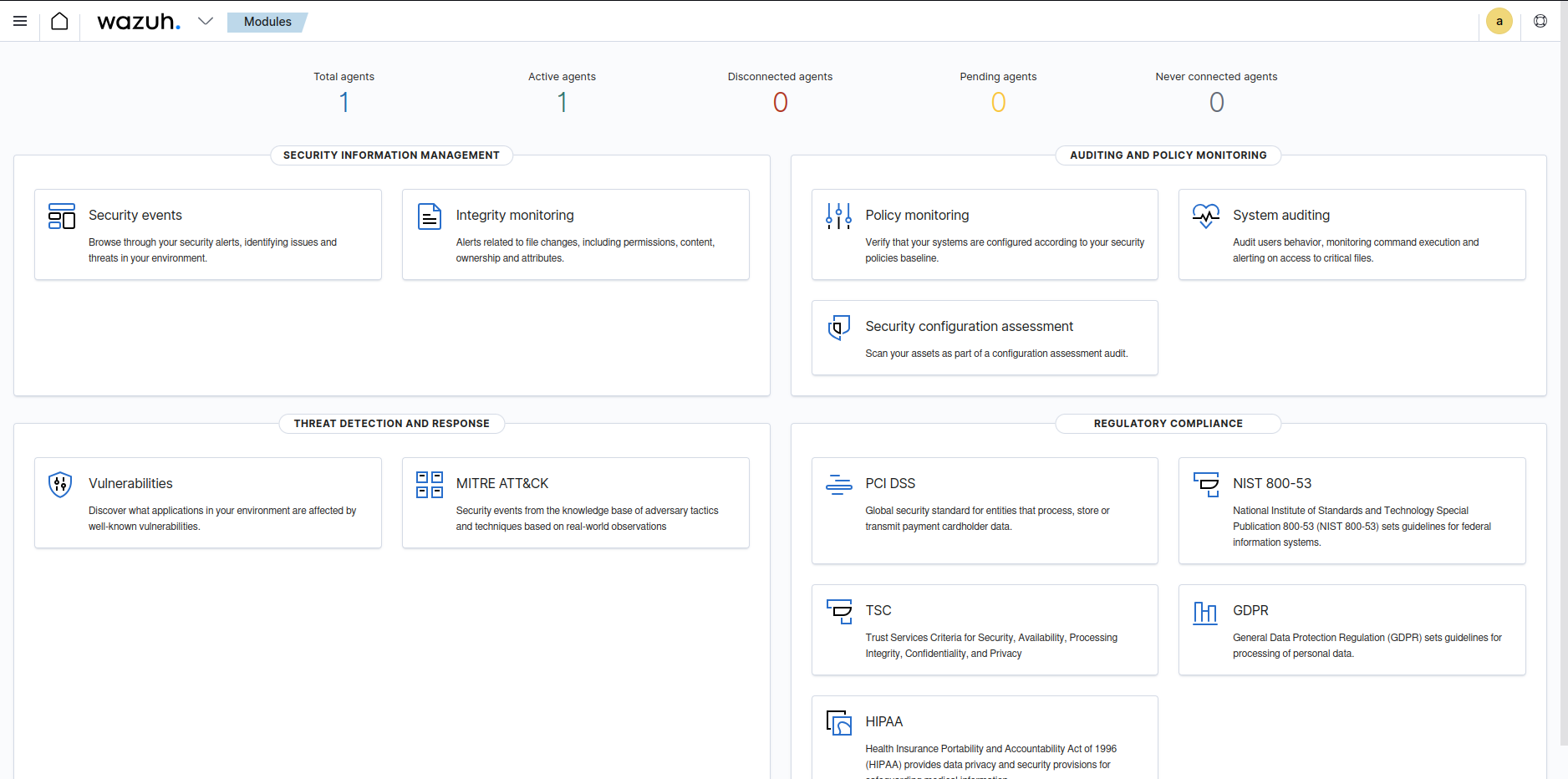
Section titled “Cyber Platform Center”It offers a set of Cyber Security platforms used for several purposes (i.e., defensive), as DefectDojo, GreenBone and Wazuh.
Configure Wazuh
Section titled “Configure Wazuh”Wazuh is an open source security platform that provides an unified XDR and SIEM protection for workloads across on-premises, virtualized, containerized, and cloud-based environments. It is used for threat prevention, detection, and response.
It consists of an endpoint security agent, deployed to the monitored systems, and a management server, which collects and analyzes data gathered by the agents.
Athena Cyber Hub makes Athena OS to be the Wazuh Management Server to collect centrally all information about threats and vulnerabilities through all endpoints where you deployed Wazuh agents.
Wazuh Management Server can be initiated easily on Athena OS by starting its container in Athena Cyber Hub. If you wish to monitor a particular system, as a Windows, MacOS or a Linux distribution system, and taking their threat and vulnerability information, how can you do it?
You need to deploy the Wazuh agent on the interested machines. You can deploy it in different manner, based on the OS of the target endpoint. For several OS, like Debian, Alpine, Windows and MacOS, Wazuh, by the Management Server, already provides agent files to deploy to the target machine.
For other systems not listed there, like Arch-based distros, the agent can be built from source directly on the target machine.
To monitor Athena OS itself, deploy the Wazuh agent as follows:
sudo pacman --needed --noconfirm -Syu curl gcc make sudo wget expect gnupg perl-base perl fakeroot python brotli automake autoconf libtool gawk libsigsegv nodejs base-devel inetutils cmakecurl -Ls https://github.com/wazuh/wazuh/archive/v4.5.2.tar.gz | tar zxcd wazuh-4.5.2sudo ./install.shYou will be asked to initialize Wazuh agent:
- Choose your preferred language or press Enter to select English as default language
- What kind of installation do you want? agent
- Choose where to install Wazuh: press Enter to select the default directory /var/ossec
- What’s the IP Address or hostname of the Wazuh server? localhost
- For the remaining options, you can answer as you wish or press Enter to select the default choice
The build process will start and after some minutes, if everything is fine, you should get a message like:
Done building agent
Wait for success...successand press Enter when asked to back to the shell. Finally, run:
sudo /var/ossec/bin/wazuh-control startand you should get:
Starting Wazuh v4.5.2...Started wazuh-execd...Started wazuh-agentd...Started wazuh-syscheckd...Started wazuh-logcollector...Started wazuh-modulesd...Completed.If Wazuh is still not started on Athena Cyber Hub, start it and wait for 2-3 minutes for its initialization. After that, open the browser and navigate to https://localhost. You should get Wazuh login page where to type the default access credentials admin:SecretPassword and, once landed on Wazuh dashboard, you should see the Active agents number to 1, that is the Wazuh agent just installed.
Unleash Athena OS to be your Blue Team OS! Monitor your OS and your infrastructure for vulnerabilities and threats in order to be always aware of your security posture!
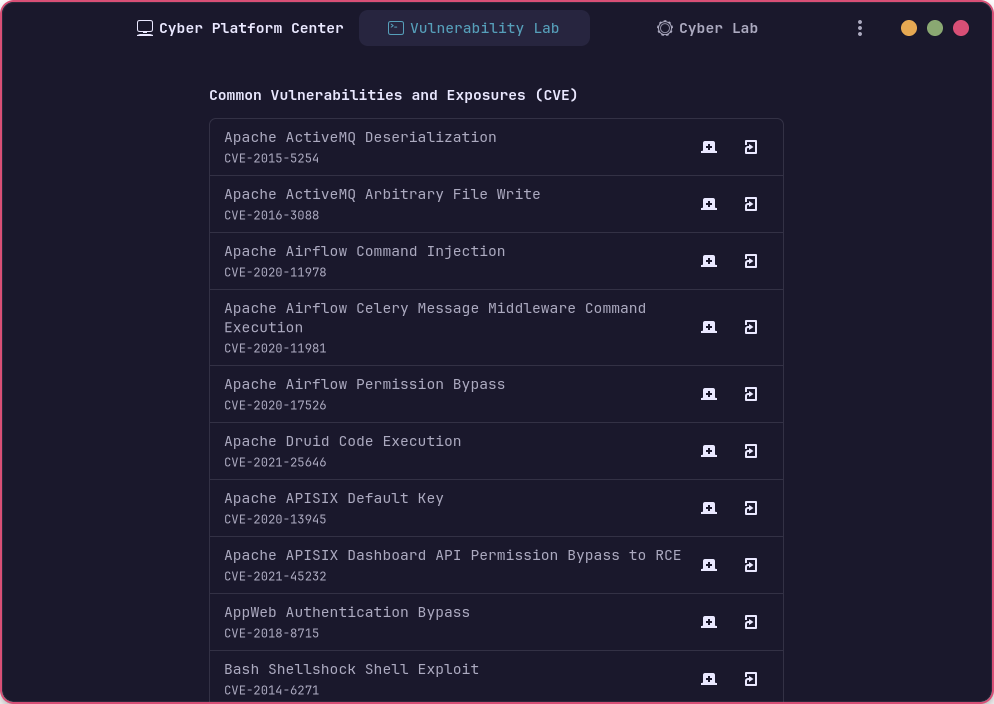
Vulnerability Lab
Section titled “Vulnerability Lab”It contains several CVE laboratories from Vulhub where you can train on real CVEs to exploit technologies and services. Furthermore, it provides also several OWASP machines to enjoy with. Run your favourite vulnerable environment and get your CVE!
Cyber Lab
Section titled “Cyber Lab”Set your custom containers and manage them in a centralized manner! When ACH is run for the first time, it will create ~/.config/athena-cyber-hub/cyberlab.toml configuration file. Edit it by inserting the required information about your container, and then run ACH. Your containers will be collected in Cyber Lab section.
Example configuration file:
[[environment]]id = "vulhub/activemq"name = "ActiveHello"path_docker = "/usr/share/athena-platform-center/vulhub/activemq/CVE-2015-5254/docker-compose.yml"path_readme = "/usr/share/athena-platform-center/vulhub/activemq/CVE-2015-5254/README.md"
[[environment]]id = "well-hub/yourlab"name = "Container 2"path_docker = "/path/to/docker-compose.yml"path_readme = "/path/to/README.md"Since Athena Cyber Hub contains README.md files with the instructions and code to exploit the vulnerable machines, they could trigger antimalware solutions, also if used in Windows as WSL, but these alerts are false positive.